This past weekend, I had the opportunity to compete in the GoldRush Gauntlet CTF, a 32-hour capture-the-flag competition hosted by the Cyberhawks at the University of North Georgia. The event was intense, fast-paced, and full of tough challenges—but most of all, it was incredibly rewarding. I'm proud to share that my team placed 9th overall out of 20 competing teams!
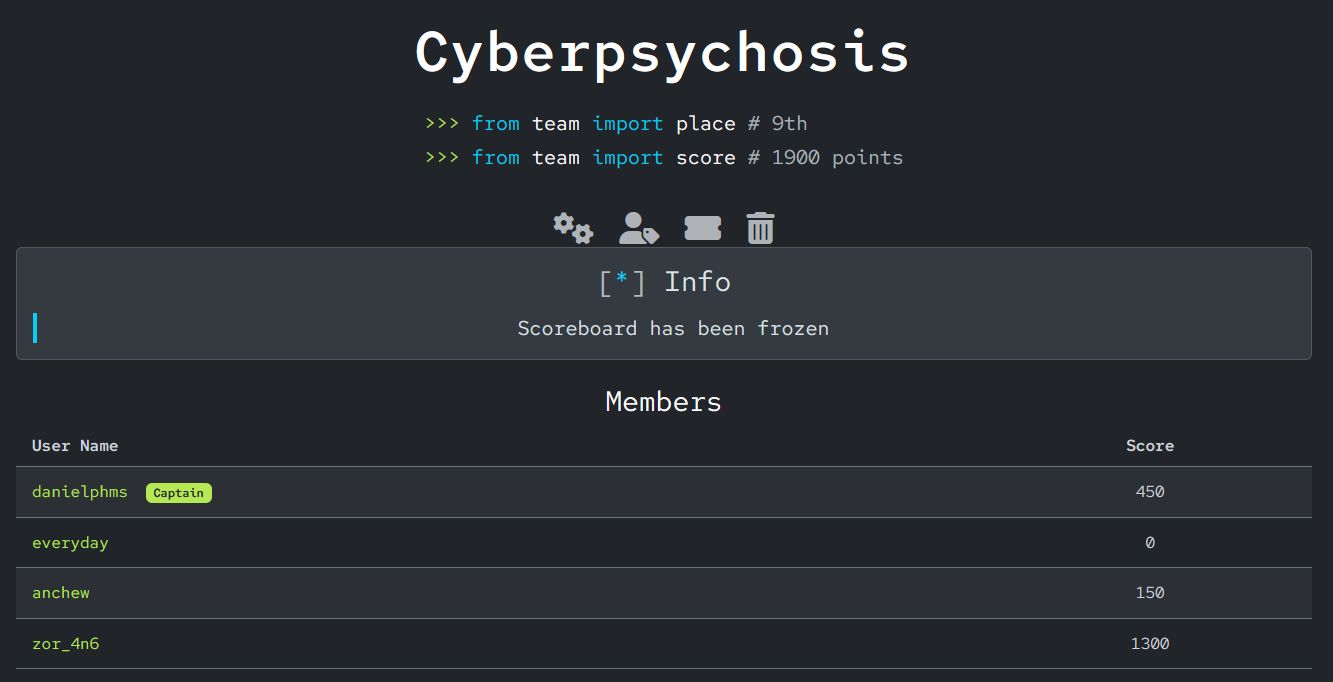
My squad, Allen Chang, Fateh Hassani, Andrew Miller, and myself, pushed through long hours of reversing, exploiting, and problem solving. This was also Allen’s(everyday) very first CTF, and while he didn’t score any points this time around, I was really glad to help him get his footing. We went over key concepts, broke down some of the challenges together, and I know he walked away with valuable takeaways. It’s awesome to see someone take their first step into the CTF space and I’m excited to see where he goes from here.
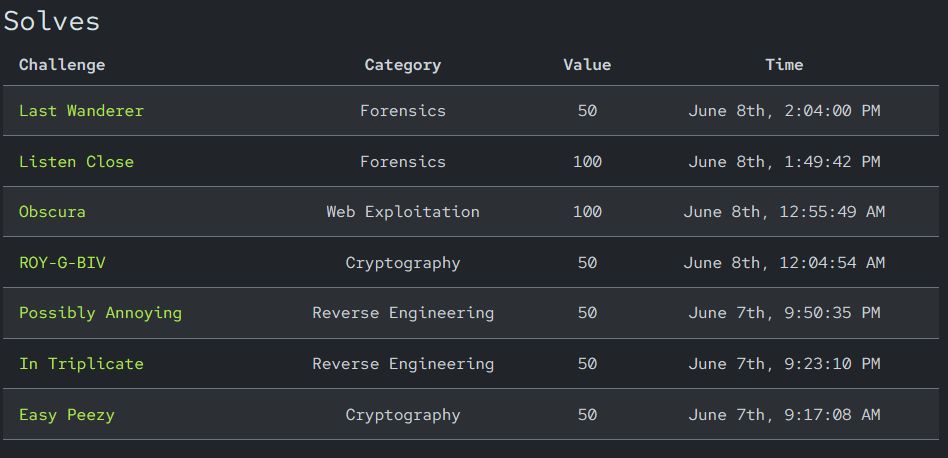
I had more reverse engineering in me, but unfortunately, I lost my Kali VM file mid-competition. Still, proud of what I managed to solve before that curveball hit.
Massive shout out to the students behind Cyberhawks for putting together such a well organized and challenging CTF. From the scenario design to the variety of problems across categories, it was clear how much work went into making this event something special.Already looking forward to next year and even more challenges to come.
← Back